Cyberpunk 2077: Hacking Guide
Hacking is one of the main skills in Cyberpunk 2077. With it, you can open locked doors, manipulate opponents, cars or cameras.
- Mini-Hacker game - Breach Protocol
- Breach Protocol - example
- Best perks - Breach Protocol
- Hacking - how does it work?
- Development of hacking
- Hacking - who is affected?
- RAM and hacking
- Quickhacking
- Quickhacks - how to get new ones?
Mini-Hacker game - Breach Protocol

Hacking is presented as a short mini-game. Its duration will depend on the situation and what you want to hack.

To make it easier for you to familiarize yourself with this system, we described it in a few simple steps. This way, you will find out what to do and will be able to get through all the hacking in your way.
Let's start with a simple explanation of the mechanics. Breach Protocol is a short mini-game, which requires a thorough analysis and clicking the relevant elements.

The first thing you need to know is that your task is to reproduce a sequence of the numbers on the right - we have marked them on the screen above.
The sequences correspond to a hacking program - a daemon.
The second thing, this mini-game resembles sudoku. Your next selected number must be in the same row or column. Otherwise you will not be able to activate it.
It is up to you which column you activate.

The third thing to remember. The first move is most important. It is up to it which next column will be activated.

Fourth thing, your buffer is limited. The buffer determines how many moves you can make. If you make too many of them, the mini-game will end, but you will not be able to hack the item.
Buffers are located on the right side, at the top. We marked it on the screen above.

Fifth thing, you can highlight the symbols you are interested in on the matrix. All you have to do is hover the daemons, and they will show up on the matrix. This can make your task easier.
Breach Protocol - example
To make sure you 100% understand what this hacker mini-game is all about, we will show you an easy example.

Look right at the daemons that are most important in this situation. These are the elements that you have to mark.
Look up on the buffer. This is the number of chances you have.
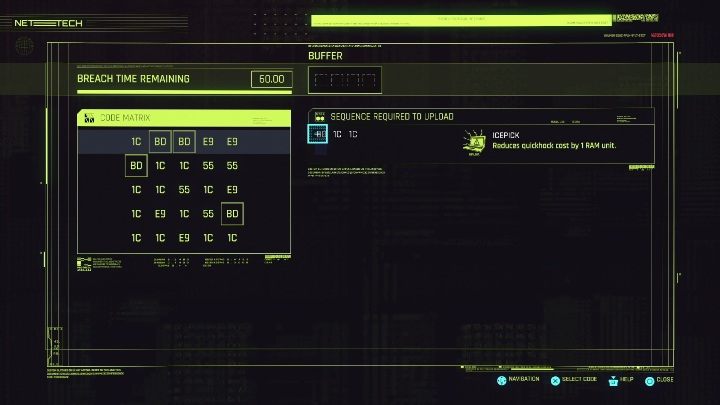
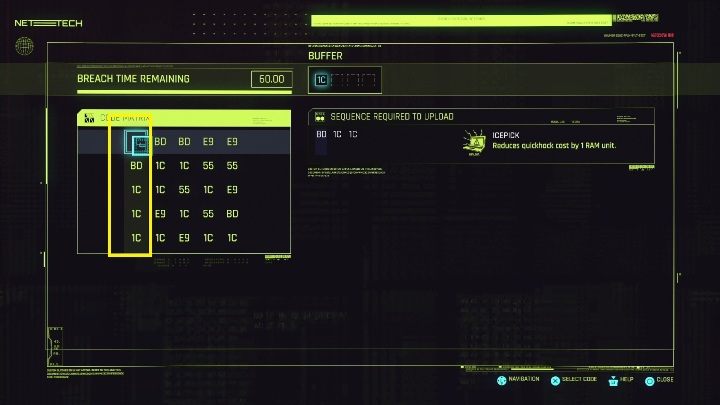
Next step. Let's go to the code's matrix.
The first symbol is BD. On the matrix you can find as many as 4. However, you must choose one that will lead you to the 1C symbols. It's the second point you have to mark. Remember, however, that you have to move from 1C to the next 1C.
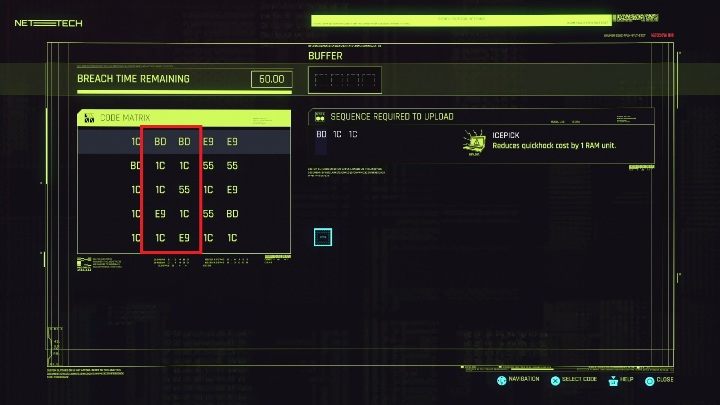
Your task is to find such a BD symbol, which is in the same column as 1C.
In this case, the second and third column will work well.

In the second column you have three 1C symbols. Take a close look at the rows they are in. Find one in which there is another 1C to complete the task.
In this case, each of the three rows will work perfectly. You can see on the screen above how easy it is to find the matching elements. Even if they are further away, all that's important that they are in one row, and you can use them.

After starting all the daemons, you will finish the mini-game successfully.
Best perks - Breach Protocol

In order to purchase the perks for the Breach of Protocol you must:
- Enter the Intelligence attribute;
- In Breach Protocol tab.
When it comes to the perks that will directly influence the mini-game, they are as below:
Head Start - this automatically activates the first daemon from the list;
Compression - the length of the daemon sequence is reduced by 1;
Transmigration - when hacking, the time increases by 50%.
Hacking - how does it work?

Hacking requires composure and calm. It is best if you try to move quietly so as not to be detected.
If you want to learn more about stealth, please visit the Stealth and quiet combatpage.

If you want to hack something, scan your surroundings first. Available objects will be highlighted. When you focus on one of them you will see a list of available battle hacks that will affect the behavior of the object.
Development of hacking

The development of hacking depends on many factors. They are affected by many variables that may limit you, such as RAM.
If you want to get serious about hacking you have to invest in:
- Attributes developing hacking;
- Attributes that reduce the level of used RAM;
- Attributes that increase the level of intelligence;
- Cyber software.
Hacking - who is affected?
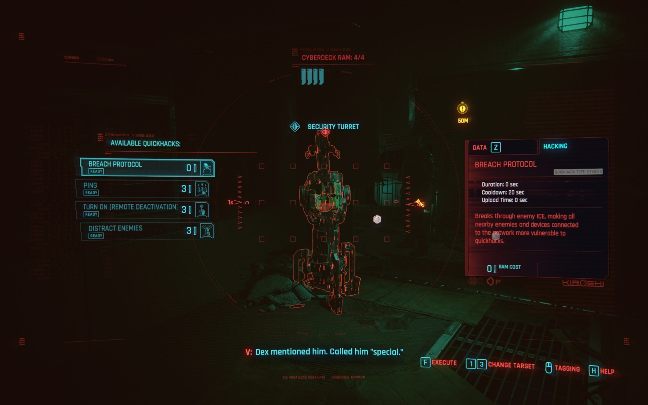
In the game you can hack different objects and characters. However, you can't treat everyone in the same way, each object has its own specific capabilities that you can do.
Remember that your hacking depends on the attributes you develop and your experience level. Some things can only be performed after unlocking a certain ability.
RAM and hacking

RAM memory is a resource used during combat hacking. Each combat hacking of an enemy or object takes a certain amount of RAM.
The cost of RAM lost during quockhacking can be adjusted by gaining new abilities and levels.
You increase the maximum amount of RAM by purchasing new attributes for intelligence and cyber software.
Additionally, it is worth remembering that you recover RAM if you do not take part in a fight.
If you want to learn more about attributes, have a look at our tutorial page, where we have described the most important perks in detail.
Quickhacking

Quickhacking is a list of actions you can perform on a given object/enemy. They appear after a device or a character is highlighted on the scanner. This list is not always the same. A lot depends on the object you are trying to hack.
If you want to learn more about the actions you can perform with hacking, have a look at a separate page, where we have described in detail the full list of available hacks in the game.
Quickhacks - how to get new ones?

You can get new quickhacks in several ways:
- Buying from vendors you find while travelling around the world;
- As rewards for completing missions.
- Cyberpunk 2077 Guide
- Cyberpunk 2077: Game Guide
- Cyberpunk 2077: Basics
- Cyberpunk 2077: Tips and tricks
- Cyberpunk 2077: Character development Guide
- Cyberpunk 2077: Difficulty levels
- Cyberpunk 2077: Skills and implants
- Cyberpunk 2077: Reputation - Street Cred
- Cyberpunk 2077: Combat and stealth
- Cyberpunk 2077: Equipment
- Cyberpunk 2077: Exploration guide
- Cyberpunk 2077: Vehicles and garage
- Cyberpunk 2077: Easter eggs list
- Cyberpunk 2077: Character creation
- Cyberpunk 2077: Hacking Guide
- Cyberpunk 2077: Quickhacking - action list
- Cyberpunk 2077: Statuses, effects - hacking
- Cyberpunk 2077: Mini-games
- Cyberpunk 2077: Crafting and weapon upgrades
- Cyberpunk 2077: Theft and other crimes
- Cyberpunk 2077: Multiplayer
- Cyberpunk 2077: Photo Mode
- Cyberpunk 2077: Braindance Guide
- Cyberpunk 2077: Death and its consequences
- Cyberpunk 2077: Stealth & quiet combat guide
- Cyberpunk 2077: GOG Awards
- Cyberpunk 2077: Factions - general information
- Cyberpunk 2077: Traders
- Cyberpunk 2077: V's Apartment
- Cyberpunk 2077: Quick scanning
- Cyberpunk 2077: XP and loot farming
- Cyberpunk 2077: Conversations with NPCs, dialogue options
- Cyberpunk 2077: User interface Guide
- Cyberpunk 2077: Quest types
- Cyberpunk 2077: Best perks
- Cyberpunk 2077: Best origins
- Cyberpunk 2077: Best modifications
- Cyberpunk 2077: Best quickhacks
- Cyberpunk 2077: Best Cyberdecks
- Cyberpunk 2077: Best cyberwares
- Cyberpunk 2077: Basics
- Cyberpunk 2077: Game Guide
You are not permitted to copy any image, text or info from this page. This site is not associated with and/or endorsed by the developers and the publishers. All logos and images are copyrighted by their respective owners.
Copyright © 2000 - 2025 Webedia Polska SA for gamepressure.com, unofficial game guides, walkthroughs, secrets, game tips, maps & strategies for top games.
