AMD Like Intel: Ryzens 5000 With Serious Security Vulnerability
AMD confirms that the new line of processors based on Zen 3 is vulnerable to a Spectre attack. The reason is the optimization mechanism included in the Ryzen 5000 and Epyc processors, among others.
- The latest AMD processors from the Zen 3 generation are vulnerable to Spectre attacks;
- The PSF optimization feature is responsible for this, but disabling it does not result in a significant performance drop.
The Spectre vulnerability, which until now was a characteristic of older Intel and ARM processors, has now also been confirmed on AMD. This is due to the new PSF (Predictive Store Forwarding) feature present in Zen 3 processors. Their optimization mechanism contains a vulnerability through which security measures can be bypassed.
AMD has published a document reporting that the company is aware of the vulnerability in the microarchitecture of the PSF hardware optimization. This is a new feature that appeared in Zen 3 chips, and it aims to speed up their operation by predicting certain actions in the processor's instruction stack. Sometimes this prediction leads to errors through which it is possible to run malicious code and read the contents of memory. For those interested - it is described in more detail in this file.

The most vulnerable is software that uses sandboxes in security processes. Applications that use hardware isolation are not vulnerable. AMD discovered that isolation of addressing protects against this type of attacks. Of course you can always disable the PSF. And it turns out that it's not such a bad idea at all. Although AMD does not recommend it, claiming the threat is low to begin with.
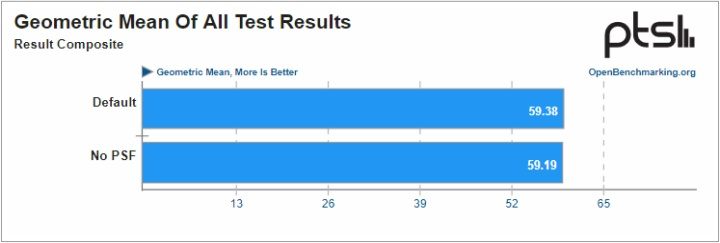
The results of tests performed and published by Phoronix show that the performance drop when PSF is turned off is minimal. Dozens of different benchmarks were performed using various Ryzen 5000 and Epyc 7003 series processors on a Linux platform. The average performance drop was less than one percent and can be assumed irrelevant.
- World’s Most Powerful Quantum Computer Can’t Run Classic Doom
- Issues with Steam Guard code? We will help you
- Tokyo Xtreme Racer (TXR) - console (PS5, PS4, Switch) release explained
- Can RX 580 GPU run Spider-Man 2? We have some good news for you
- How to get inZOI Creative Studio key. Don't miss this early access