Valorant Cheats Will Steal Your Passwords
Security analysts have detected a password-stealing program in cheats for Valorant. Scammers exploit players willing to cheat in games by placing malware in the file.
2

Korean security analysts detect malware in cheats for Valorant that are distributed on YouTube. The creators of such videos easily bypass the website's control measures and persuade players to download the program stealing information.
Data stealing
Korean analysts from ASEC have detected malware contained in cheats for Valorant. The aiming assistance app is available through YouTube.
Users who download the file found in the video's description will be redirected to anonfiles page with a RAR archive containing the file "Cheat installer.exe". It is actually a link to RedLine Stealer, a software designed to steal passwords.
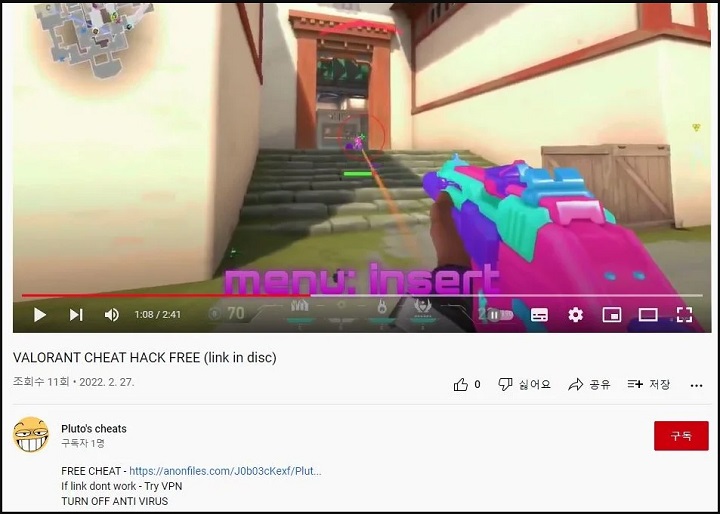
RedLine Stealer steals the following data
- Basic information: Computer name, user name, IP address, Windows version, computer information (CPU, GPU, RAM, etc.), and process list.
- Web Browsers: Passwords, credit card numbers, AutoFill forms, bookmarks and cookies from Chrome, Chrome-based browsers, and Firefox.
- Cryptocurrency wallets: Armory, AtomicWallet, BitcoinCore, Bytecoin, DashCore, Electrum, Ethereum, LitecoinCore, Monero, Exodus, Zcash, and Jaxx.
- VPN Client: ProtonVPN, OpenVPN and NordVPN.
- Other: FileZilla (host address, port number, username and passwords), Minecraft (account details), Steam (client session), Discord (token information).
After collecting this information, RedLine packs it into ZIP archives and sends it to a Discord server using a WebHook API POST request.
More for You:
- Gamers Cheat Because They Get Frustrated With Other Cheaters, Time2play Reports
- Elden Ring's PC Anti-cheat Gives Hope for Cheater-free Fun
- Cheat Creator Ceases His 'Support' for Battlefield 2042
Do not trust links from YouTube
Cheating in video games, apart from taking the fun out of the game and spoiling the gameplay for others, is also a security risk.
Tools of this type are not created by trustworthy entities and do not have a digital signature, thus - in most cases - they have unwanted software. ASEC's report is just a drop in the ocean of such malicious practices preying on people's ignorance.
2
Latest News
- This is expected to be the biggest year in the company's history. Blizzard prepares an offensive that will overshadow previous years
- Bethesda envied CD Projekt RED? Starfield may undergo a Cyberpunk 2077-style metamorphosis
- Season 2 has just started, and Todd Howard is already writing the script for the third one. Fallout 5 will be changed by the TV show
- 5 games to grab on Amazon Prime Gaming. Among them, a collection of RPG classics
- My experience attending the 2025 Game Awards, and why I loved it


